How to Disable HSTS (Strict‑Transport‑Security) in Chrome
Learn step-by-step how to disable HSTS settings in Chrome. This guide helps you resolve the “Your connection is not private” error and troubleshoot issues in local development environments.
At times, while developing locally or debugging a specific site, you may encounter a message like “Your connection is not private” and find yourself blocked from accessing the page. One common cause of this is the HSTS (HTTP Strict Transport Security) policy. While this is an essential feature for security, there are occasions during development when it needs to be temporarily disabled.
In this post, we’ll briefly explain what HSTS is and guide you step-by-step through multiple methods to disable it in Chrome. Use this guide to cleanly resolve HSTS-related errors and boost your development efficiency!
What is HSTS and Why Should You Disable It?
sequenceDiagram
participant User as 🧑 User (Browser)
participant Server as 🌐 Web Server
participant Attacker as 🚫 MITM Attacker
Note over User,Server: ① User first accesses the site via HTTPS
User->>Server: HTTPS request (GET https://example.com)
Server-->>User: Response + Strict-Transport-Security header<br/>(max-age=31536000)
Note over User: ② Browser stores HSTS policy<br/>(Only HTTPS allowed for one year)
User-x Attacker: ❌ Blocks HTTP access attempts (prevents MITM attacks)
User->>Server: ✅ All future requests use HTTPS only
Server-->>User: Returns secure response
HSTS is a web security policy that forces the browser to use only encrypted HTTPS protocol when communicating with a specific website. It works by the web server sending a special HTTP header that tells the browser, “From now on, only communicate with me over HTTPS!” This effectively prevents security threats like man-in-the-middle (MITM) attacks.
However, this strong security feature can be a hindrance for developers. For instance, during testing in local development environments where HTTPS isn’t required, the HSTS policy can forcibly block access. In such cases, it’s necessary to temporarily disable HSTS for smoother testing and debugging.
How to Disable HSTS in Chrome
There are several effective ways to disable HSTS settings in Chrome. Follow these steps starting from the most common method.
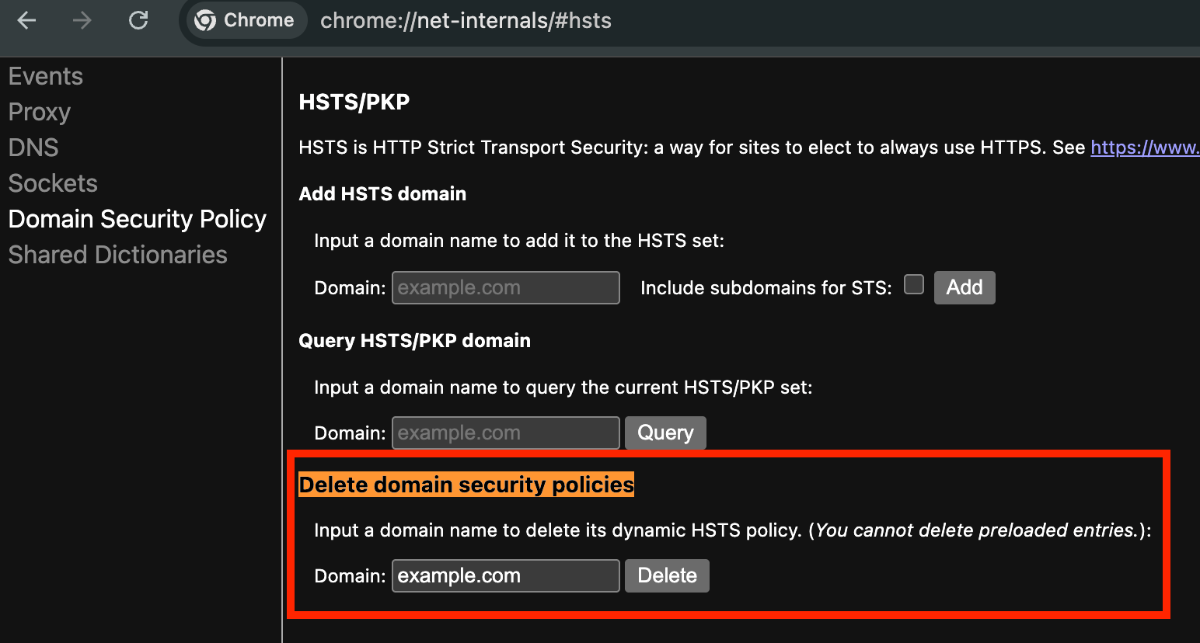
1. Remove Settings via chrome://net-internals
This is the most direct and reliable method. You can access Chrome’s internal settings page to delete the HSTS policy for a specific domain.
-
Type
chrome://net-internals/#hstsinto the Chrome address bar and press Enter. -
Find the Delete domain security policies section.
-
Enter the domain name you want to delete HSTS settings for (e.g.,
example.com) in the Domain input field. -
Click the Delete button on the right.
Now, the HSTS settings for that domain have been deleted. To verify, use the Query HSTS/PKP domain section to check the domain—if it shows “Not found,” you’re all set! 😊
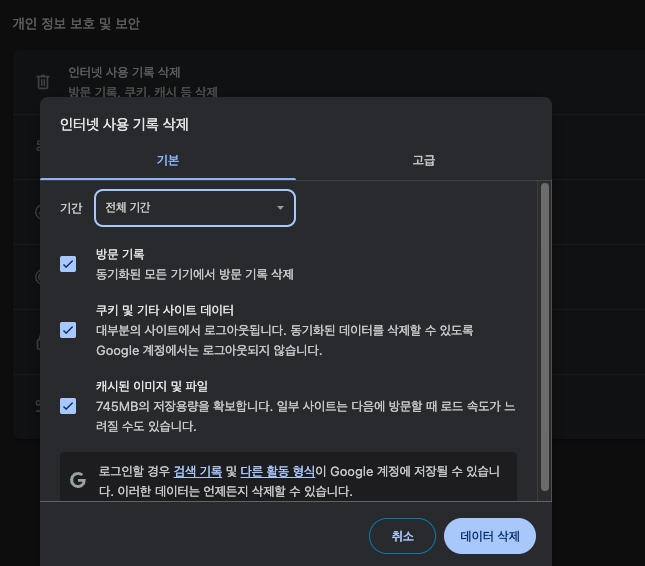
2. Clear Chrome’s Cache and Cookies
If the net-internals method doesn’t work, HSTS data may still be stored in the browser cache.
-
Go to Chrome settings (
chrome://settings). -
Click “Clear browsing data” under the “Privacy and security” section.
-
Set the “Time range” to “All time.”
-
Check the boxes for “Cookies and other site data” and “Cached images and files,” then click the “Clear data” button.
Note that this method also deletes login info and data for other sites, so use it carefully.
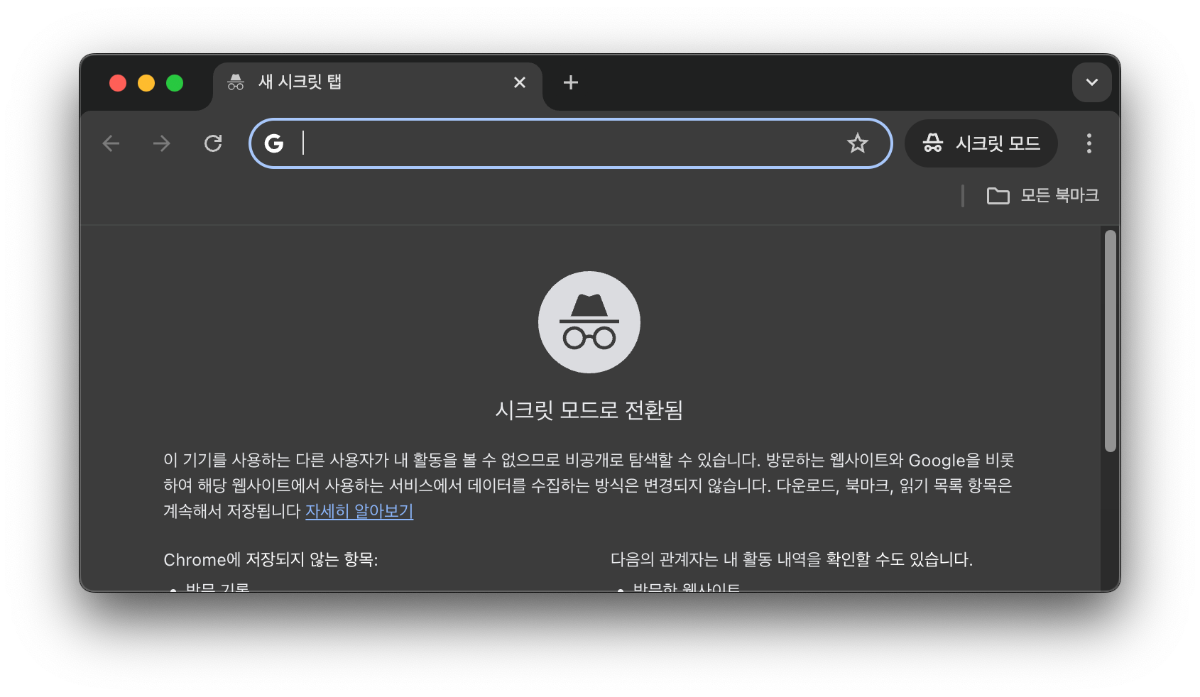
3. Use Incognito Mode
A simple temporary workaround. Incognito mode typically doesn’t apply cached HSTS settings or use extensions, so HSTS policies often don’t apply.
Try opening the page in Incognito mode (shortcut: Ctrl+Shift+N or Cmd+Shift+N). If it works, the issue likely lies with your existing browser’s cache or an extension.
4. Reset Your Router
If none of the above methods work and you’re still seeing the “Your connection is not private” error, your Wi-Fi router’s DNS settings might have been tampered with—this is sometimes called “pharming.”
Try holding down the Reset button on the back or bottom of your router for about 10 seconds to reset it. If the problem persists, contact the router manufacturer’s support to reinstall the firmware.
Limitations and Key Considerations
Before disabling HSTS, it’s important to understand a few crucial points.
Preloaded Domains
Google maintains a built-in list in Chrome via hstspreload.org for certain domains. If a domain (e.g., google.com, facebook.com) is on this preload list, HSTS cannot be disabled using net-internals. You can check if a domain is on the preload list by visiting the HSTS Preload List website.
Security Risks
HSTS is a critical security feature. It should only be disabled temporarily for development or debugging purposes, and always re-enabled once the task is complete. Disabling HSTS and browsing over an insecure network could expose you to security threats.
Troubleshooting Common Issues
Disabling HSTS might trigger other types of errors.
-
Certificate errors: If the error mentions HSTS, privacy certificates, or incorrect names, check your computer’s date and time settings. Also, antivirus software’s “HTTPS protection” or “HTTPS inspection” features might conflict with Chrome’s security functions—try disabling them temporarily.
-
Extension conflicts: If the issue is resolved in Incognito mode, one of your Chrome extensions may be causing it. Visit
chrome://extensions, and disable them one by one to identify the culprit.
Balancing Development Efficiency and Security
We’ve now looked at various methods to disable the HSTS policy in Chrome. In most cases, using chrome://net-internals is the simplest fix, but there could be other factors like cache or network issues.
HSTS is an important technology that makes the web more secure. Still, developers need flexibility at times. Keep today’s tips in mind so you can quickly and accurately handle HSTS-related issues during development. And once you’re done, don’t forget to restore the settings for better security!